The Modern Wax Seal
for the Digital Age
The Modern Wax Seal
for the Digital Age
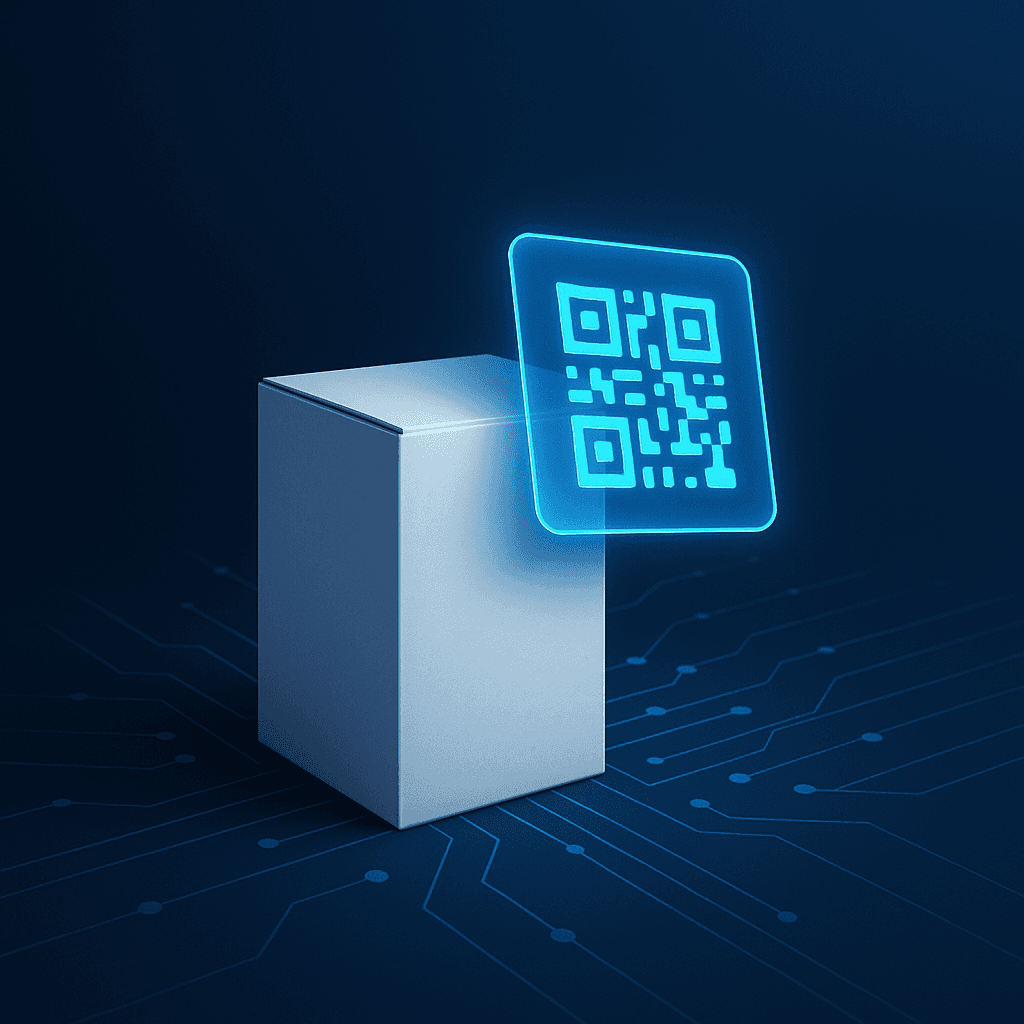
Zortag provides tamper-resistant, non-clonable labels and ID cards that link physical documents, permits, and credentials to secure digital originals. Instantly verifiable by smartphone, backed by immutable audit trails.
Zortag provides tamper-resistant, non-clonable labels and ID cards that link physical documents, permits, and credentials to secure digital originals. Instantly verifiable by smartphone, backed by immutable audit trails.








250+ Satisfied Users
Companies That Trust Us


The Modern Wax Seal
for the Digital Age
Zortag provides tamper-resistant, non-clonable labels and ID cards that link physical documents, permits, and credentials to secure digital originals. Instantly verifiable by smartphone, backed by immutable audit trails.




250+ Satisfied Users
Companies That Trust Us

What We Do
Innovative Asset Security Solutions
Revolutionizing asset protection with cutting-edge technology, ensuring unparalleled transparency and trust in a rapidly evolving digital landscape.
Anti-Counterfeiting Protection
Anti-Counterfeiting Protection
Anti-Counterfeiting Protection
Safeguard Your Brand
Safeguard Your Brand
Safeguard Your Brand



Art and Asset Authentication
Art and Asset Authentication
Art and Asset Authentication
Preserve the Authenticity and Value of Assets
Preserve the Authenticity and Value of Assets
Preserve the Authenticity and Value of Assets



Anti-Diversion Measures
Anti-Diversion Measures
Anti-Diversion Measures
Ensure Product Integrity
Ensure Product Integrity
Ensure Product Integrity



Document Verification
Document Verification
Document Verification
Verify Documents with confidence
Verify Documents with confidence
Verify Documents with confidence



Evidence Verification and Tracking
Evidence Verification and Tracking
Evidence Verification & Tracking
Streamline and Secure Your Evidence Verification and Tracking
Streamline & Secure Your Evidence Verification and Tracking
Secure Your Evidence Verification & Tracking



Blockchain Security
Blockchain Security
Blockchain Security
Provide Digital certificates of authenticity
Provide Digital certificates of authenticity
Provide Digital certificates of authenticity



And so many more…
The Difference We Make
Physical-Digital Identification Products
We are transforming how industries protect their products, brands, and consumers in a world where trust is paramount.
The Difference We Make
Physical-Digital
Identification Products
We are transforming how industries protect their products, brands, and consumers in a world where trust is paramount.
Asset Identification, Verification, and Authentication
Secure ID Labels
Zortag Secure ID Labels
Ensure authenticity by securely linking your products, documents, or other assets to secure digital information and blockchain-based certificates of authenticity.
Unclonable 3D Optical Fingerprint
Instant Authenticity Verification
Access Secure Information
Tamper-Evident
Location Tracing



Multi-Factor Identification and Multi-Level Access
Controlled Access Cards
Manage user-specific access and permissions to secure information and digital systems such as email accounts, crypto accounts, digital assets, or whatever you can imagine.
Biometrically-Secure
NFC-enhanced
Multi-level Information Access
Connection to Community
Scan Location Tracking
How it Works
How it Works
Zortag Label Authentication
Easy 1-2 Process
Set up Label



Step 1
Setup Label Authentication
Set up multi-level information, links, etc, to display after a successful label authentication scan.
Set up multi-level information, links, etc, to display after a successful label authentication scan.


Step 2
Tag Item
Apply tamper-resistant labels to your item to link it to secure label authentication.
Apply tamper-resistant labels to your item to link it to secure label authentication.
Scan to Authenticate



Step 1
Scan to Authenticate
Scan the label with a mobile device to confirm the authenticity of documents, products, assets, etc.
Scan the label with a mobile device to confirm the authenticity of documents, products, assets, etc.



Step 2
Access Information & Links
View secure authentication information, links, and images related to that item.
View secure authentication information, links, and images related to that item.
Our Features
Features of Zortag Secure id labels

Tamper-Resistant Design
Non-cloneable 3D optical fingerprints ensure unique asset identification.

Secure Access Control
Non-cloneable 3D optical fingerprints ensure unique asset identification.

Choose a Plan
Non-cloneable 3D optical fingerprints ensure unique asset identification.

Unique Identification
Provide a distinct, non-replicable identifier for each asset.

Subscribe Instantly
Provide a distinct, non-replicable identifier for each asset.

Subscribe Instantly
Provide a distinct, non-replicable identifier for each asset.

Document and Asset Verification
Verify the authenticity of documents or assets, ensuring they haven't been tampered with or counterfeited.

Subscribe Instantly
Verify the authenticity of documents or assets, ensuring they haven't been tampered with or counterfeited.

Subscribe Instantly
Verify the authenticity of documents or assets, ensuring they haven't been tampered with or counterfeited.
Comprehensive Metadata Storage
Include detailed asset history, such as weight, purity, and origin.

Get Tailored Solutions
Include detailed asset history, such as weight, purity, and origin.

Get Tailored Solutions
Include detailed asset history, such as weight, purity, and origin.

Integration with Blockchain
Links physical assets to immutable digital certificates.

Receive Your Supplies
Links physical assets to immutable digital certificates.

Receive Your Supplies
Links physical assets to immutable digital certificates.

Trace
Monitors scan locations and frequencies for enhanced security insights.

Choose a Plan
Monitors scan locations and frequencies for enhanced security insights.

Choose a Plan
Monitors scan locations and frequencies for enhanced security insights.

Communicate
Facilitate ongoing engagement with customers and users.

Get Tailored Solutions
Facilitate ongoing engagement with customers and users.

Get Tailored Solutions
Facilitate ongoing engagement with customers and users.
Our Features
Features of ZorCard

Inclusive Secure ID Features
integrates all Zortag label features, including unique identification and blockchain security, for seamless and trusted authentication.

Subscribe Instantly
integrates all Zortag label features, including unique identification and blockchain security, for seamless and trusted authentication.

Subscribe Instantly
integrates all Zortag label features, including unique identification and blockchain security, for seamless and trusted authentication.

Secure Access Control
Grants or restricts access to physical locations, systems, or digital platforms, ensuring only authorized individuals can enter.

Secure Access Control
Grants or restricts access to physical locations, systems, or digital platforms, ensuring only authorized individuals can enter.

Choose a Plan
Grants or restricts access to physical locations, systems, or digital platforms, ensuring only authorized individuals can enter.

Identity Verification
Quickly verifies an individual's identity when scanned or tapped against a compatible reader.

Subscribe Instantly
Quickly verifies an individual's identity when scanned or tapped against a compatible reader.

Subscribe Instantly
Quickly verifies an individual's identity when scanned or tapped against a compatible reader.

Contactless Payments
Facilitate secure, contactless payment transactions, with authentication provided through the card's unique credentials.

Get Tailored Solutions
Facilitate secure, contactless payment transactions, with authentication provided through the card's unique credentials.

Get Tailored Solutions
Facilitate secure, contactless payment transactions, with authentication provided through the card's unique credentials.

Digital Authentication
Stores digital certificates or tokens that provide authentication for online services or applications, enhancing security.

Receive Your Supplies
Stores digital certificates or tokens that provide authentication for online services or applications, enhancing security.

Receive Your Supplies
Stores digital certificates or tokens that provide authentication for online services or applications, enhancing security.
Multi-Factor Authentication
Acts as a factor in multi-factor authentication systems, requiring both the card and another authentication method.

Choose a Plan
Acts as a factor in multi-factor authentication systems, requiring both the card and another authentication method.

Choose a Plan
Acts as a factor in multi-factor authentication systems, requiring both the card and another authentication method.
Membership and Loyalty Programs
Store membership information, providing easy access to member services and benefits.

Get Tailored Solutions
Store membership information, providing easy access to member services and benefits.

Get Tailored Solutions
Store membership information, providing easy access to member services and benefits.

Data Encryption & Secure Storage
Protects encrypted data, ensuring privacy and security.

Receive Your Supplies
Protects encrypted data, ensuring privacy and security.

Receive Your Supplies
Protects encrypted data, ensuring privacy and security.
Users









